Show:
7 Layers of Cybersecurity Explained: A Complete Guide
Imagine going through security at the airport where they only check your ticket—no metal detectors, no cameras, no checking of prohibited items in your luggage. Would you feel secure up on that plane? Probably not. You expect layers of security measures at the airport for passenger safety. In the digital world, cybersecurity works the same way. It’s not enough to have a single defense.
With cyber threats becoming more sophisticated every day, understanding the layers of cybersecurity is crucial for protecting your digital assets. It minimizes the risk of breaches and criminals trying to hack your system.
This guide explores the essential layers of cybersecurity and how they work together to create a robust defense against cyber threats.
The Seven Layers of Cybersecurity
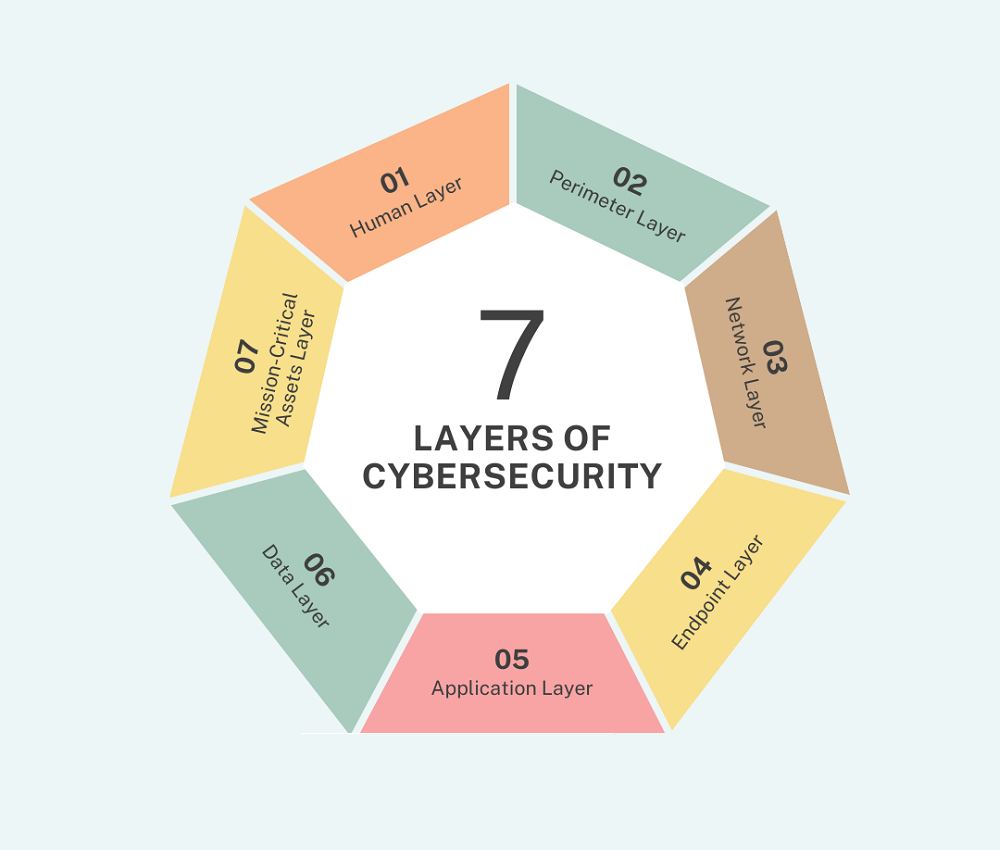
The seven layers of cybersecurity refer to a structured approach that breaks down the different areas of protection required to secure systems, networks, and data from cyber threats. Rather than relying on a single tier of security, these cybersecurity levels work together to ensure that all potential attack vectors are covered. Here’s a breakdown of the seven layers:
1. Human Layer
The Human Layer in cybersecurity focuses on the people who interact with systems, networks, and data. And humans err and can be manipulated, which is why this layer is considered the weakest link in cybersecurity. Whether it’s clicking on phishing emails, using weak passwords, or being tricked by social engineering attacks, human error often causes security breaches. Hackers know this and trick people into bypassing standard security protocols. That’s why addressing the Human Layer is crucial in any cybersecurity strategy.
To protect the Human Layer, several key security measures must be put in place:
- Security Awareness Training: People should be educated to spot and respond to threats. Regular awareness sessions on how to recognize phishing, malware, and social engineering attacks are a great way to do that.
- Strong Password Policies: Encouraging people to use strong passwords, alongside multi-factor authentication (MFA), is also a must to add an extra layer of security.
- Security Culture: Make security a part of your daily operations and overall culture so that everyone understands the importance of cybersecurity and knows how to report suspicious activities.
2. Perimeter Layer
The Perimeter Layer acts as the outermost defense for a network. It protects the boundary between internal systems and the external world, such as the Internet. This layer keeps unwanted traffic, attackers, and malicious activity from entering the internal network by blocking malicious activity before it reaches deeper systems. This is why implementing strong security measures at this layer is essential to protect the overall integrity of the network and prevent breaches.
To protect the Perimeter Layer effectively, the following security measures must be a part of your security strategy:
- Firewalls: Think of Firewalls as the gatekeepers of the system. They control and monitor the flow of traffic in and out of the network. By enforcing predefined security rules, firewalls help prevent unauthorized access and block harmful traffic.
- Intrusion Detection/Prevention Systems (IDS/IPS): Implementing IDS/IPS solutions that monitor network activity for unusual or suspicious behavior. IDS alerts you to potential threats, while IPS actively takes steps to block them.
- Network Access Control (NAC): Restricting access to the network based on device compliance with security policies, ensuring only authorized, secure devices can connect.
3. Network Layer
The Network Layer secures the internal network itself by monitoring and controlling the flow of data. It allows secure communication between devices and systems within an organization, ensuring that information reaches the right destination while maintaining secure internal traffic. This layer restricts access to authorized users only, preventing unauthorized access and potential data breaches. Since it handles large amounts of sensitive information, it’s a critical part of network security layers designed to protect data integrity across the entire network.
These key strategies are essential for securing the Network Layer:
- Segmentation: Breaking the network into smaller segments, such as with VLANs, limits the impact of an attack and offers better control over access to critical areas.
- Encryption: Encrypting both internal and external data traffic using methods like TLS, IPsec, and VPNs to protect information while it’s in transit.
- Network Monitoring: Using network traffic tools to continuously monitor and detect irregular patterns, and identify potential threats for a proactive security response.
Understanding your network’s defenses is key, and similarly, individuals should be aware of their own online presence; you can check your IP and examine your online anonymity using dedicated tools.

4. Endpoint Layer
Any device such as a laptop or phone that’s connected to a network, can be an easy entry point for attackers. The Endpoint Layer focuses on protecting these individual devices (endpoints). These devices act as gateways to the network and in most cases are the first point of contact between users and the system. Securing them is critical. Because if compromised, these devices can give hackers access to the entire network.
Ensuring strong security at the Endpoint Layer through these measures is crucial to preventing breaches and protecting sensitive data:
- Antivirus and Anti-malware: Utilizing updated antivirus and anti-malware software to shield endpoints from malicious software.
- Endpoint Detection and Response (EDR): Implementing tools that offer real-time monitoring and response to detect and address threats on endpoints immediately.
- Patch Management: Regularly updating software and operating systems to patch known vulnerabilities, reducing the risk of exploitation by attackers.
5. Application Layer
The Application Layer is where users interact directly with the software; hence, all systems will have an Application Layer. This layer contains web browsers, email clients, and other applications that process sensitive information and perform essential functions. An attack on this layer is often a result of flaws in application design or coding that make the application vulnerable.
Important security protocols are needed for the detection of potential vulnerabilities, integrity of applications, and data protection. These include:
- Application Security Testing: Performing both static and dynamic testing to identify and remove vulnerabilities in the application code before attackers can exploit them.
- Web Application Firewalls (WAF): Protecting web applications by filtering and monitoring HTTP traffic, helping to block malicious attempts to compromise the application.
- Secure Development Practices: Following secure coding guidelines, such as those provided by OWASP, throughout the software development lifecycle to minimize vulnerabilities and create safer applications.
6. Data Layer
The Data Layer perhaps is the most important in this layered security model that focuses on protecting the data itself—at rest (stored data) or even while in transit (data being transferred over a network). It deals with sensitive information, such as financial records, customer information, and even intellectual property, thereby making it a prime target for cybercriminals. A breach at this level can cause heavy financial and reputational losses, including data theft or corruption if proper layered security is not in place.
To effectively protect the Data Layer, different levels of cybersecurity should be implemented:
- Encryption: Sensitive data should be encrypted at rest and in transit. At rest, encryption requires AES-256, while in-transit encryption requires TLS 1.2/1.3 to maintain confidentiality.
- Data Classification: Sensitive data should be classified as public, confidential, or restricted and have appropriate controls applied to each classification level.
- Access Controls: Implement role-based access control (RBAC) by allowing only authorized people to access sensitive data. This reduces the likelihood of unauthorized exposure across the network security layers at large.

7. Mission-Critical Assets Layer
The Mission-Critical Assets Layer is all about protecting the important information assets and data of an organization. These are the assets that, if compromised, could seriously impact the organization. For example, for a hospital, mission-critical assets might include patient records, medical devices, and appointment scheduling systems. Losing access to these could delay patient care, disrupt daily operations, and even lead to legal issues. Protecting these core assets is a must.
To protect mission-critical assets, several key security measures should be in place:
- Backup and Recovery: Regularly back up mission-critical assets and test recovery processes to reduce the impact of ransomware or data loss.
- Disaster Recovery and Business Continuity Plans: Have contingency plans to ensure operations can continue during a cyberattack or data loss, ensuring minimal downtime.
- Multi-layered Defense: Implement multiple security controls, such as network segmentation, encryption, and strict access controls, to protect mission-critical systems and create redundancy for better protection.
How to Effectively Implement A Layered Cybersecurity System
A poorly executed layered cybersecurity system is no different from having no security protocol at all. Implementing a layered security to protect your IT environment involves four steps: evaluating the risks and systems; defining the needs; developing a strategy; and routine monitoring and assessment.
The first stage begins with a thorough evaluation of not just the existing tools and systems, but also of any potential vulnerabilities and security threats within those systems.
The second step is to define what you want to protect and achieve from your cybersecurity plan. Once you know these two, you can proceed to develop a strategy with specific actions and timelines. That will be the crux of your layered cybersecurity system.
The most important step of an effective layered security system is to routinely monitor and assess your strategy. Identifying weak links and updating security to stay ahead of evolving threats.
Conclusion
It is clear that a strong cybersecurity strategy should be multi-tiered, as relying on a single layer of defense is not enough. The safety measures and cybersecurity examples mentioned above like awareness training, intrusion detection systems, segmentation, and encryption are different tactics that can work together to maximize system and data security. Organizations can protect their systems and stay ahead of threats by assessing risks, setting clear goals, and implementing layered cybersecurity defenses. But that’s not all! An effective cybersecurity strategy needs proactiveness which means regularly reviewing and improving these measures to ensure you’re not just reacting to risks but actively defending against them.

 Return to Previous Page
Return to Previous Page








